Quick! The bad guy/super villain has left the room! Plug in a mysterious device that’ll hack up their computer while an on-screen progress bar ticks forward to convey to the audience that things are working!
It’s a classic scene from basically every spy movie in history. In this case, however, that mystery device is real.
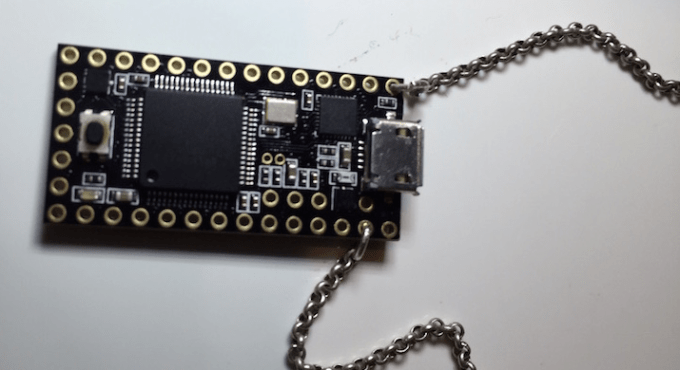
Samy Kamkar — developer of projects like that massive worm that conquered MySpace back in 2006, or SkyJack, the drone that hijacks other drones — has released a video demonstrating the abilities of a particularly ridiculous “necklace” he sometimes wears around.
Called USBdriveby, it’s a USB-powered microcontroller-on-a-chain, rigged to exploit the inherently awful security flaws lurking in your computer’s USB ports. In about 60 seconds, it can pull off a laundry list of nasty tricks:
It starts by pretending to be a keyboard/mouse.
If you have a network monitor app like Little Snitch running, it uses a series of keystrokes to tell LittleSnitch that everything is okay and to silence all warnings.
It disables OS X’s built-in firewall.
It pops into your DNS settings and tweaks them to something under the hacker’s control, allowing them to replace pretty much any website you try to visit with one of their own creation.
It opens up a backdoor, then establishes an outbound connection to a remote server which can send remote commands. Since the connection is outbound, it eliminates the need to tinker with the user’s router port forwarding settings.
It closes any windows and settings screens it opened up, sweeping up its footprints as it heads for the door.
So in 30-60 seconds, this device hijacks your machine, disables many layers of security, cleans up the mess it makes, and opens a connection for remote manipulation even after the device has been removed. That’s… kind of terrifying.
While the video above focuses on OS X, the methods tapped here aren’t exclusive to Apple’s platform. Kamkar says everything shown so far is “easily extendable to Windows or *nix.”
So what can you do to protect yourself from things like this? Not a whole lot, really — that’s why attacks like this and BadUSB are so freaky. A lot of these flaws are inherent to the way the USB protocol was designed and implemented across so many hundreds of millions of computers; short of filling your USB ports with cement or never, ever leaving your computer’s ports unattended while out and about, there’s no magic fix.
Comments
Post a Comment