Malware that takes computers hostage until users pay a ransom is getting meaner, and thanks to the growing prevalence of Bitcoin and other digital payment systems, it's easier than ever for online crooks to capitalize on these "ransomware" schemes. If this wasn't already abundantly clear, consider the experience of Nic, an Ars reader who fixes PCs for a living and recently helped a client repair the damage inflicted by a particularly nasty title known as CryptoLocker.
It started when an end user in the client's accounting department received an e-mail purporting to come from Intuit. Yes, the attached archived zip file with an executable inside should have been a dead giveaway that this message was malicious and was in no way affiliated with Intuit. But accounting employees are used to receiving e-mails from financial companies. When the receiver clicked on it, he saw a white box flash briefly on his screen but didn't notice anything else out of the ordinary. He then locked his computer and attended several meetings.
Within a few hours, the company's IT department received word of a corrupt file stored on a network drive that was available to multiple employees, including the one who received the malicious e-mail. A quick investigation soon uncovered other corrupted files, most or all of which had been accessed by the accounting employee. By the time CryptoLocker had run its course, hundreds of gigabytes worth of company data was no longer available.
"After reading about the ransomware on reddit earlier this week, we guessed [that it was] what we were dealing with, as all the symptoms seemed to be popping up," Nic, who asked that his last name not be published, wrote in an e-mail to Ars. "We went ahead and killed the local network connection on the machine in question and we were immediately presented with a screenshot letting us know exactly what we were dealing with."
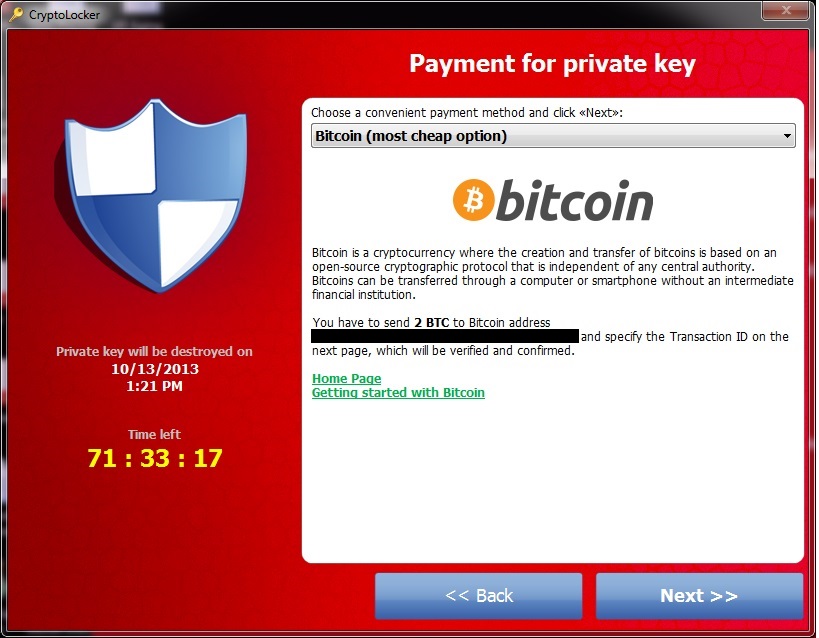
According to multiple participants in the month-long discussion, CryptoLocker is true to its name. It uses strong cryptography to lock all files that a user has permission to modify, including those on secondary hard drives and network storage systems. Until recently, few antivirus products detected the ransomware until it was too late. By then, victims were presented with a screen like the one displayed on the computer of the accounting employee, which is pictured above. It warns that the files are locked using a 2048-bit version of the RSA cryptographic algorithm and that the data will be forever lost unless the private key is obtained from the malware operators within three days of the infection.
“Nobody and never will be able to restore files”
"The server will destroy the key after a time specified in this window," the screen warns, displaying a clock that starts with 72:00:00 and counts down with each passing second. "After that, nobody and never will be able to restore files. To obtain the private key for this computer, which will automatically decrypt files, you need to pay 300 USD / 300 EUR / similar amount in another currency."
None of the reddit posters reported any success in breaking the encryption. Several also said they had paid the ransom and received a key that worked as promised. Full backup files belonging to Nic's clients were about a week old at the time that CryptoLocker first took hold of the network. Nic advised them to comply with the demand. The ransomware operators delivered a key, and about 24 hours later, some 400 gigabytes of data was restored.
CryptoLocker accepts payment in Bitcoins or through the MoneyPak payment cards, as the following two screenshots illustrate.